Videos
Product Details
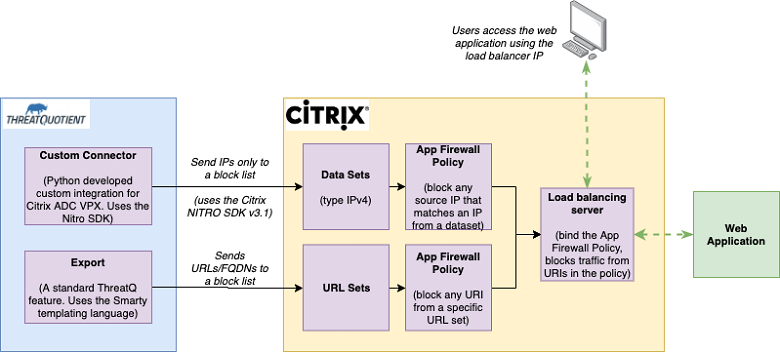
The integration between ThreatQ and Citrix enables threat analysts to send indicators of compromise from ThreatQ to a Citrix ADC VPX appliance, and use those indicators in policies to control traffic coming from them to web applications protected by the VPX appliance.
ThreatQ is security operations and threat intelligence platform that allows analysts to Specifically, it is used to
- Collect indicators of compromise from threat feeds, SIEMs, and sensors
- Deduplicate, relate and store threat objects in a Threat Library
- Enrich indicators from various sources
- Conduct threat investigations within the platform
- Disseminate indicators to network devices (e.g. firewalls, proxies), SIEMs, and ticketing platforms
ThreatQ has two distinct methods for integrating with Citrix – a Custom connector and an Export.
Custom connector
The custom connector takes IPv4 indicators of compromise curated by analysts in a saved search on ThreatQ and sends them to a designated Data Sets list on the Citrix appliance. The flexibility of the connector allows analysts to define their own criteria for the saved search, the ability of the integration to read from multiple saved searches and the ability to use a customer-defined name for the Citrix Data Set. All of the configuration parameters needed are done via the ThreatQ UI and can easily be modified.
The custom connector is developed in Python 2.7 and it uses the Citrix NITRO SDK v3.1 library to communicate with the Citrix API. It installs via pip install, and once installed it needs to be configured via the ThreatQ UI.
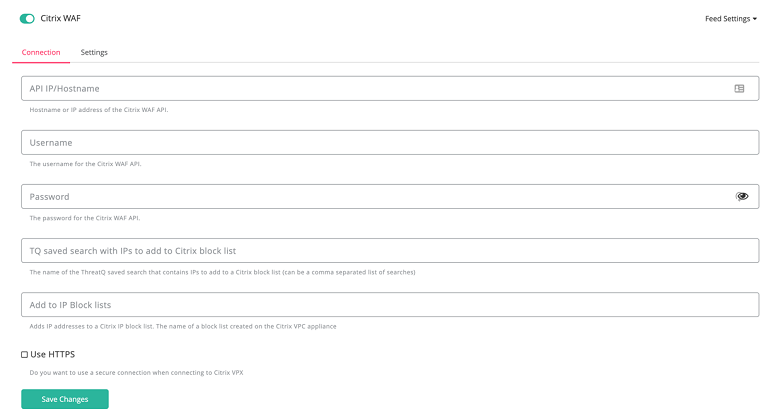
Below is a snapshot of the configuration required in the ThreatQ UI with a description of each of the values needed to setup the connector.
- API IP/Hostname: Hostname or IP address of the Citrix VPX instance
- Username: The username for the Citrix VPX instance
- Password: The password for the Citrix VPX instance
- Saved Search: The name(s) of the saved search in the ThreatQ instance. This can be a comma-separated list of saved searches
- IP Block List: The name of a block list created on the Citrix VPX appliance in the Data Sets feature
- Use HTTPS: Check this box if the connection to the Citrix VPX appliance is secure
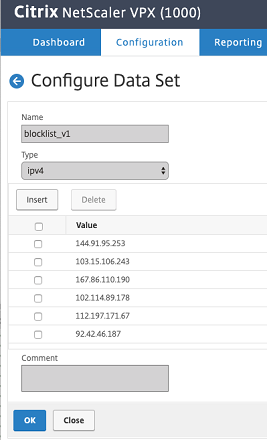
The connector executes from the ThreatQ command line, which can be configured as a cron job. Once it finishes execution, all the IPv4 indicators pushed to Citrix will be available in the data set provided in the ThreatQ UI.
The attached snapshot shows indicators in the “blocklist_v1” in the Data Sets.
Export
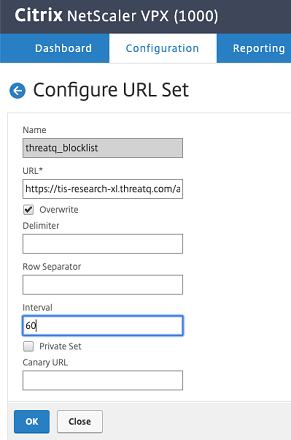
The Export is a core ThreatQ functionality which integrates with the Citrix URL Sets feature. Using the ThreatQ UI, users can define their own search criteria, and export all of the indicators that match that criteria to an endpoint. Once created, the endpoint can be added to the URL Sets in Citrix and configured so that it is periodically polled, and any new indicators are downloaded to Citrix.
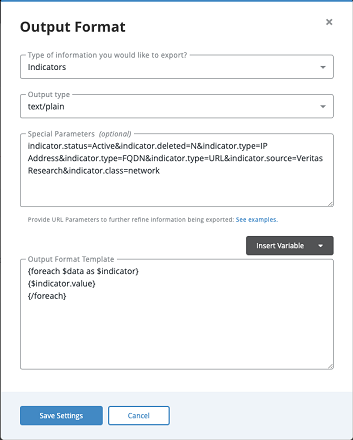
Adding a differential parameter will force the export to output only the indicators created after the last time the export URL was refreshed.
An export uses the Smarty templating language. The attached example matches all active indicators of the type IP, FQDN and URL, and outputs them to a list available via an endpoint with the format: https:///api/export//?limit=10&token=
The endpoint is added to the URL Sets in Citrix, and all the indicators are imported and become available for creating security policies.
Screenshots